Oh guys. I always used panels with fail2ban included but now I have no panel, installed fail2ban and configured but it doesn't work properly. I mean yeah it works but doesn't work after I reboot my server or after the first fail to login. Where did I go wrong way?
@Anon said:
Oh guys. I always used panels with fail2ban included but now I have no panel, installed fail2ban and configured but it doesn't work properly. I mean yeah it works but doesn't work after I reboot my server or after the first fail to login. Where did I go wrong way?
Find out that everythings work on Ubuntu 18.04. But not on Ubuntu 20.04. Checked bug reports, found this https://bugs.launchpad.net/ubuntu/+source/fail2ban/+bug/1875169
Checked and it turned out I have this recommended line already, so nothing to change
Anyone facing the issue with fail2ban on Ubuntu 20.04?
@Anon said:
Oh guys. I always used panels with fail2ban included but now I have no panel, installed fail2ban and configured but it doesn't work properly. I mean yeah it works but doesn't work after I reboot my server or after the first fail to login. Where did I go wrong way?
Find out that everythings work on Ubuntu 18.04. But not on Ubuntu 20.04. Checked bug reports, found this https://bugs.launchpad.net/ubuntu/+source/fail2ban/+bug/1875169
Checked and it turned out I have this recommended line already, so nothing to change
Anyone facing the issue with fail2ban on Ubuntu 20.04?
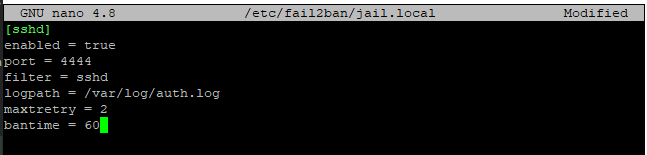
I think you might need to set the bantime to 3600 instead of 60 if you are looking for a 1-hour ban.
Edit: a 60 second ban explains why works, then doesn't, but I do not know why you are allowed to exceed your maxretry of 2 unless the banaction (iptables-multiport or ufw/auto) is disabled.
Even when tcp port is not listened an icmp packet is sent back to caller saying: nobody here... Usually, I setup firewall to allow access to ssh port from my networks only and black holing the unused port ranges. The bunch of scanners are setup to rescan all internet on a daily if not an hour basis.
@Anon said:
Oh guys. I always used panels with fail2ban included but now I have no panel, installed fail2ban and configured but it doesn't work properly. I mean yeah it works but doesn't work after I reboot my server or after the first fail to login. Where did I go wrong way?
Use fail2ban-regex to see what is being matched in the logs rather than blindly guessing.
@tetech said:
Use fail2ban-regex to see what is being matched in the logs rather than blindly guessing.
@MaxKVM said: I think you might need to set the bantime to 3600 instead of 60 if you are looking for a 1-hour ban.
Edit: a 60 second ban explains why works, then doesn't, but I do not know why you are allowed to exceed your maxretry of 2 unless the banaction (iptables-multiport or ufw/auto) is disabled.
But everything works fine on Ubuntu 18.04 with the same config. 60 secs just to test.
Looks like your were right with iptables-multiport things. Tried to fix it by adding
To jail.local
But it didn't help
Then tried banaction = iptables-allports instead of iptables-multiport and still facing the same issue...
Any idea? I'm not good at iptables at all, only ufw.
/etc/fail2ban/action.d/iptables-common.conf file
# Option: lockingopt
# Notes.: Option was introduced to iptables to prevent multiple instances from
# running concurrently and causing irratic behavior. -w was introduced
# in iptables 1.4.20, so might be absent on older systems
# See https://github.com/fail2ban/fail2ban/issues/1122
# Values: STRING
lockingopt = -w
This one option with deleting -w I also tried, commenting this line as well
@tetech said:
Use fail2ban-regex to see what is being matched in the logs rather than blindly guessing.
@MaxKVM said: I think you might need to set the bantime to 3600 instead of 60 if you are looking for a 1-hour ban.
Edit: a 60 second ban explains why works, then doesn't, but I do not know why you are allowed to exceed your maxretry of 2 unless the banaction (iptables-multiport or ufw/auto) is disabled.
But everything works fine on Ubuntu 18.04 with the same config. 60 secs just to test.
Looks like your were right with iptables-multiport things. Tried to fix it by adding
To jail.local
But it didn't help
Then tried banaction = iptables-allports instead of iptables-multiport and still facing the same issue...
Any idea? I'm not good at iptables at all, only ufw.
I would try to set banaction = ufw if you are using ufw. This should be the default on Ubuntu 20.04 though. Is your ufw enabled?
It wasn't installed by that time. Just a fresh VPS. I started from the fail2ban configurating and stuck...
Installed now, allowed 22/tcp, enabled, added banaction = ufw to jail.local, restarted f2b, even rebooted the vps. Nothing interesting.
Looks like works, banned me 2 times after the each 3th attempt. Restarted the VPS and again it wasn't working. Okay.
systemctl enable fail2ban
Rebooted and now it's working. Dunny why so complicated on 20.04... when on 18.04 was sooo smooth
root@lowend: iptables-save
# Generated by iptables-save v1.8.4 on Tue Jul 21 14:13:07 2020
*filter
:INPUT ACCEPT [6:422]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [4:324]
:f2b-sshd - [0:0]
-A INPUT -p tcp -m multiport --dports 22 -j f2b-sshd
-A f2b-sshd -j RETURN
COMMIT
# Completed on Tue Jul 21 14:13:07 2020
===================================
root@lowend: iptables -nvL
Chain INPUT (policy ACCEPT 69 packets, 5271 bytes)
pkts bytes target prot opt in out source destination
89 9740 f2b-sshd tcp -- * * 0.0.0.0/0 0.0.0.0/0 multiport dports 22
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 53 packets, 8617 bytes)
pkts bytes target prot opt in out source destination
Chain f2b-sshd (1 references)
pkts bytes target prot opt in out source destination
65 7888 RETURN all -- * * 0.0.0.0/0 0.0.0.0/0
==================================
root@lowend:~# fail2ban-client status sshd
Status for the jail: sshd
|- Filter
| |- Currently failed: 1
| |- Total failed: 11
| `- File list: /var/log/auth.log
`- Actions
|- Currently banned: 0
|- Total banned: 5
`- Banned IP list:
I'm afraid that after setting UFW it will not be working lol.
And also dunno why I'm doing all this...I disabled root auth, added keys, disabled password auth. Maybe no reason having fail2ban for ssh?
Comments
Yeah. This trips you up as a noob.
Take a look at (as root) output of :
lsof -i
Oh guys. I always used panels with fail2ban included but now I have no panel, installed fail2ban and configured but it doesn't work properly. I mean yeah it works but doesn't work after I reboot my server or after the first fail to login. Where did I go wrong way?
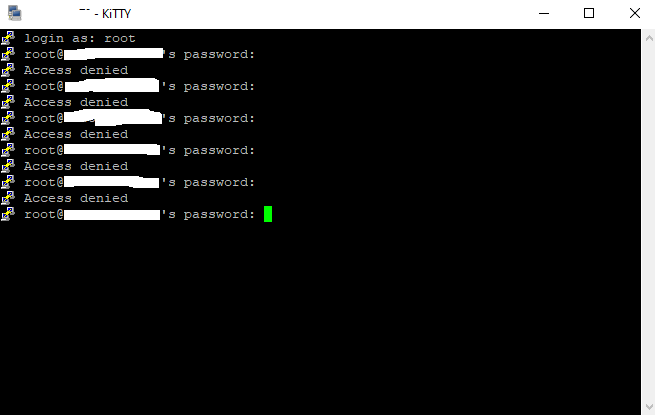
I love that idea
Find out that everythings work on Ubuntu 18.04. But not on Ubuntu 20.04. Checked bug reports, found this
https://bugs.launchpad.net/ubuntu/+source/fail2ban/+bug/1875169
Checked and it turned out I have this recommended line already, so nothing to change
Anyone facing the issue with fail2ban on Ubuntu 20.04?
I think you might need to set the bantime to 3600 instead of 60 if you are looking for a 1-hour ban.
Edit: a 60 second ban explains why works, then doesn't, but I do not know why you are allowed to exceed your maxretry of 2 unless the banaction (iptables-multiport or ufw/auto) is disabled.
AMD EPYC powered Performance NVMe VPS - Los Angeles, Dallas, New York, Amsterdam, Singapore | Support | Status
Even when tcp port is not listened an icmp packet is sent back to caller saying: nobody here... Usually, I setup firewall to allow access to ssh port from my networks only and black holing the unused port ranges. The bunch of scanners are setup to rescan all internet on a daily if not an hour basis.
Use
fail2ban-regexto see what is being matched in the logs rather than blindly guessing.But everything works fine on Ubuntu 18.04 with the same config. 60 secs just to test.
Looks like your were right with iptables-multiport things. Tried to fix it by adding
To jail.local
But it didn't help
Then tried banaction = iptables-allports instead of iptables-multiport and still facing the same issue...
Any idea? I'm not good at iptables at all, only ufw.
/etc/fail2ban/action.d/iptables-common.conf file
# Option: lockingopt
# Notes.: Option was introduced to iptables to prevent multiple instances from
# running concurrently and causing irratic behavior. -w was introduced
# in iptables 1.4.20, so might be absent on older systems
# See https://github.com/fail2ban/fail2ban/issues/1122
# Values: STRING
lockingopt = -w
This one option with deleting -w I also tried, commenting this line as well
I would try to set banaction = ufw if you are using ufw. This should be the default on Ubuntu 20.04 though. Is your ufw enabled?
AMD EPYC powered Performance NVMe VPS - Los Angeles, Dallas, New York, Amsterdam, Singapore | Support | Status
It wasn't installed by that time. Just a fresh VPS. I started from the fail2ban configurating and stuck...
Installed now, allowed 22/tcp, enabled, added banaction = ufw to jail.local, restarted f2b, even rebooted the vps. Nothing interesting.
What type of virtualization? Show
iptables-savewith your IPs redacted - possible that there's an ACCEPT before the f2b chain?KVM
With ufw enabled
The IPs aren't mine, that's why I didn't redact them
Is there anything new in fail2ban-regex now? It seems like you may have the NSA version of fail2ban.
AMD EPYC powered Performance NVMe VPS - Los Angeles, Dallas, New York, Amsterdam, Singapore | Support | Status
f2b chains don't exist, so clearly nothing is going to be blocked.
Installed inetutils-syslogd and iptables-persistent, then fail2ban and edited jail.local.
Looks like works, banned me 2 times after the each 3th attempt. Restarted the VPS and again it wasn't working. Okay.
systemctl enable fail2banRebooted and now it's working. Dunny why so complicated on 20.04... when on 18.04 was sooo smooth
===================================
==================================
I'm afraid that after setting UFW it will not be working lol.
And also dunno why I'm doing all this...I disabled root auth, added keys, disabled password auth. Maybe no reason having fail2ban for ssh?