but no, i dont care about that, i just have ssh running as an external service, the rest are interesting stories from the web, it turns out you can keep your system up to date and patched, and your provider doesn't and you still get fucked, still this is the uptime thread, not the security patch thread
For domain registrations, create an account at Dynadot (ref) and spend $9.99 within 48 hours to receive $5 DynaDollars! Looking for cost-effective Managed/Anycast/DDoS-Protected/Geo DNS Services? Try ClouDNS (aff).
@emre said:
[root@jennifer ~]# w
zero updates, zero maintenance,
At this point, there's likely several others who have root@jennifer.
I'm too cheap to pay for KernelCare on boxes where I usually tweak the kernel, so it'd be pointless anyhow. ~300 days is about the best I can do before there's something that absolutely requires a modicum of downtime to alleviate. Of course, in production, KernelCare, semi-default compatible kernel builds.
again, updating does not mean you're safe, most 0days are in the wild for months before being patched so do not expect to be bullet proof if you do that, if you want to be safe you need to add some extra stuff, like grsecurity, start a learn and set up rules in place, all services must run in dockers/lxc/chroots, for apache/nginx there is modsecurity, disabling php functions bla bla bla, it can take hours to explain how to secure a linux box and it still wont be 100% secure because there is always one flaw, a human has access to it
in my case i'm not running any external stuff except ssh so i dont care that much but my system is up to date, even if i get compromised i'll just reinstall, the idea is to have backups and not be cocky that you are some big shot sysadmin, and all will be well
If your ssh is exposed, that can be a pretty big issue. I assume you're using portknocking actively or fail2ban passiovely, but this is hardly the thread for that. We're mostly just dickwaving uptime here, and I opted to say why I don't really have more than a year to show in general. My BSD boxes can go longer than that, but they're becoming rare for forward-facing since I don't work for Netflix.
@WSS said:
If your ssh is exposed, that can be a pretty big issue. I assume you're using portknocking actively or fail2ban passiovely, but this is hardly the thread for that. We're mostly just dickwaving uptime here, and I opted to say why I don't really have more than a year to show in general. My BSD boxes can go longer than that, but they're becoming rare for forward-facing since I don't work for Netflix.
Protecting SSH + firewall takes cares of most drive-by attacks. Most of us are not high value targets.
@WSS said:
If your ssh is exposed, that can be a pretty big issue. I assume you're using portknocking actively or fail2ban passiovely, but this is hardly the thread for that. We're mostly just dickwaving uptime here, and I opted to say why I don't really have more than a year to show in general. My BSD boxes can go longer than that, but they're becoming rare for forward-facing since I don't work for Netflix.
Comments
How the security patches looking though?
grape?
HS4LIFE (+ (* 3 4) (* 5 6))
Block all the ports. Look at the blank black screen and scream hail merry 3 times.
Nexus Bytes Ryzen Powered NVMe VPS | NYC|Miami|LA|London|Netherlands| Singapore|Tokyo
Storage VPS | LiteSpeed Powered Web Hosting + SSH access | Switcher Special |
its 2019
https://ubuntu.com/livepatch
https://ksplice.oracle.com/
but no, i dont care about that, i just have ssh running as an external service, the rest are interesting stories from the web, it turns out you can keep your system up to date and patched, and your provider doesn't and you still get fucked, still this is the uptime thread, not the security patch thread
Ah, another reason for comparing our d@@ks
(Assuming everyone here has one)
Mine's pretty short, since I consider 60-day uptimes an achievement.
The all seeing eye sees everything...
13:32:12 up 693 days, 8:55, 1 user, load average: 0.00, 0.00, 0.00
HostHatch 128MB VZ in NL
For domain registrations, create an account at Dynadot (ref) and spend $9.99 within 48 hours to receive $5 DynaDollars!
Looking for cost-effective Managed/Anycast/DDoS-Protected/Geo DNS Services? Try ClouDNS (aff).
[root@jennifer ~]# w
06:49:26 up 1779 days, 12:57, 1 user, load average: 0,13, 0,22, 0,21
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
root pts/0 94.xx.xx.xx 06:49 0.00s 0.01s 0.00s w
[root@jennifer ~]# rpm -q centos-release
centos-release-6-6.el6.centos.12.2.x86_64
[root@jennifer ~]# uname -a
Linux jennifer.xxxx 2.6.32-504.8.1.el6.x86_64 #1 SMP Wed Jan 28 21:11:36 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
[root@jennifer ~]#
Hetzner dedicated box with a single site and directadmin.
zero updates, zero maintenance,
at this point this server is now in Gods hands,
if it works it works , if it dies it dies...
An old KS-3c storage box, due to be retired next month
All my favourite VPS providers would easily give me 300+ days.
I just choose to reboot once every 5-6 mos.
My longest running VPS is:
Host live migrated for patching the hosts (spectre, etc).
At this point, there's likely several others who have root@jennifer.
I'm too cheap to pay for KernelCare on boxes where I usually tweak the kernel, so it'd be pointless anyhow. ~300 days is about the best I can do before there's something that absolutely requires a modicum of downtime to alleviate. Of course, in production, KernelCare, semi-default compatible kernel builds.
My pronouns are asshole/asshole/asshole. I will give you the same courtesy.
again, updating does not mean you're safe, most 0days are in the wild for months before being patched so do not expect to be bullet proof if you do that, if you want to be safe you need to add some extra stuff, like grsecurity, start a learn and set up rules in place, all services must run in dockers/lxc/chroots, for apache/nginx there is modsecurity, disabling php functions bla bla bla, it can take hours to explain how to secure a linux box and it still wont be 100% secure because there is always one flaw, a human has access to it
in my case i'm not running any external stuff except ssh so i dont care that much but my system is up to date, even if i get compromised i'll just reinstall, the idea is to have backups and not be cocky that you are some big shot sysadmin, and all will be well
Edit: Almost forgot, it will be 2020 soon
https://www.digitalocean.com/community/tutorials/what-is-immutable-infrastructure
If your ssh is exposed, that can be a pretty big issue. I assume you're using portknocking actively or fail2ban passiovely, but this is hardly the thread for that. We're mostly just dickwaving uptime here, and I opted to say why I don't really have more than a year to show in general. My BSD boxes can go longer than that, but they're becoming rare for forward-facing since I don't work for Netflix.
My pronouns are asshole/asshole/asshole. I will give you the same courtesy.
[root@VGXG002 ~]# uptime
09:29:45 up 641 days, 16:48, 1 user, load average: 0.30, 1.65, 2.60
Leaseweb SG
UpCloud free $25 through this aff link - Akamai, DigitalOcean and Vultr alternative, multiple location, IPv6.
10:39:41 up 930 days, 1:03, 1 user, load average: 0.96, 0.73, 0.67
don't ask why and for what reason xD
Grab your vmWare toblerone today.
Protecting SSH + firewall takes cares of most drive-by attacks. Most of us are not high value targets.
Deals and Reviews: LowEndBoxes Review | Avoid dodgy providers with The LEBRE Whitelist | Free hosting (with conditions): Evolution-Host, NanoKVM, FreeMach, ServedEZ | Get expert copyediting and copywriting help at The Write Flow
I opened a thread back in the old LES forum quite some time ago. My best then was a LES VPS:
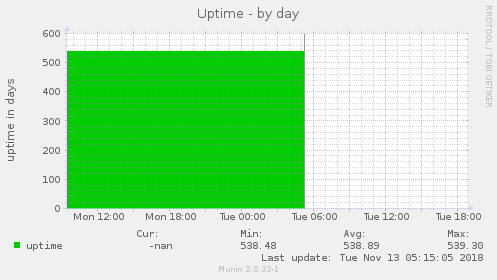
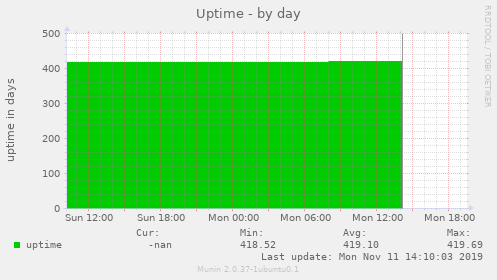
Since then, a now retired VirMach VPS achieved this:
different port, password login disabled
VPN box with @liteserver:
Idle box with Virmach:
Storage box with @AnthonySmith: